5G requires cybersecurity collaboration

Software-defined networking and virtualisation are transforming the way telecom networks are built. Networks can now be disaggregated and share a common infrastructure between multiple network function vendors. This evolution makes security management increasingly crucial to operations. Tight control is needed to apply appropriate security configurations to each interface and component of the software stack, to avoid malfunction or unauthorised access.
5G is different from previous mobile network technology in the sheer number and range of use cases it will serve across diverse industries, including mission-critical scenarios on which lives depend, such as healthcare and autonomous vehicles. Securing 5G infrastructure whilst ensuring optimal performance, speed and user experience across these emerging applications comes with new challenges.
This article will look at three key areas of security focus in a 5G connected world.
Considering network slicing
Telecommunications providers are looking to use ‘network slicing’ to support the multitude of use cases and new services that 5G can enable. Network slicing allows independent organisations to share the same physical networks in order to be more efficient with their resources. Benefits include the ability to fine-tune end user experience and network capabilities for specific scenarios or enterprise sectors.
The primary security challenge for network slicing is to ensure strong isolation between the different consumers of a sliced network in a shared environment. Each individual network slice used by customers must be properly separated from others, in order that all users across a network are sufficiently protected. In addition to supporting network isolation (and container isolation, which we will come to next), the infrastructure also needs to have technical capabilities to secure application access and data, such as authentication, authorization, encryption, and runtime observability.
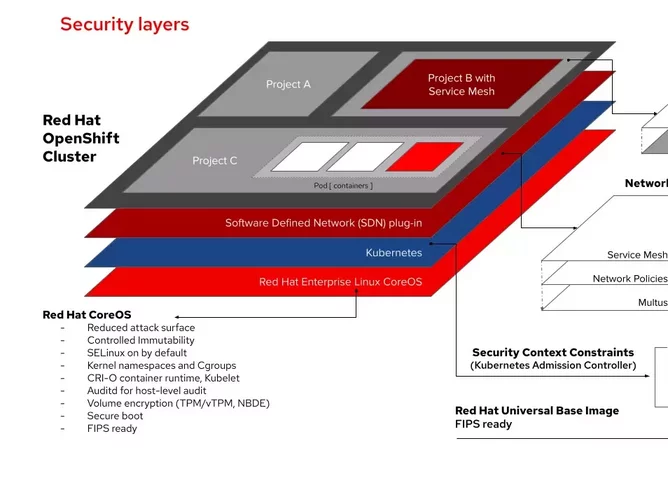
Securing containerised network functions
5G networks are rapidly moving to container-based architectures. Containers are individual applications that are deployed and run on a shared operating system without the need for virtual machines. Packaging and deploying applications as containers, which carry their own operating system dependencies and are thus abstracted from the underlying infrastructure, gives service providers more flexibility to move and scale them across a hybrid cloud environment. Deploying containers at scale requires orchestration, for which Kubernetes is now the dominant technology. Kubernetes alone does not include all security features required for 5G containerized applications, whereas there are supported, mature Kubernetes-based container platforms that do. Such features help to build security into application development, for example ensuring the use of trusted container content, as well as deployment, which means securing the Kubernetes platform as well as automating deployment policies.
Containers provide greater resource-sharing capabilities and increased portability and scalability, which in turn requires a sharp focus on how the environment is configured to reduce vulnerabilities. For example, privileges for running containers should not be granted by default: developers are no longer alone on a platform. The overriding principle should be that confidentiality and integrity is crucial, and applications should be configured to function with minimum privileges.
All this puts security automation in high demand. For example, telecommunications providers want to be able to automate the configuration and management of infrastructure for continuous compliance and to support and enable security of applications, data and attached storage. They also want to enable regular, automatic updating of software to ensure the most current protection at all times. This is why we now see a movement in the industry towards adopting DevSecOps in order to achieve automated continuous security of services, from vulnerability management, to incident detection and response, risk profiling and more.
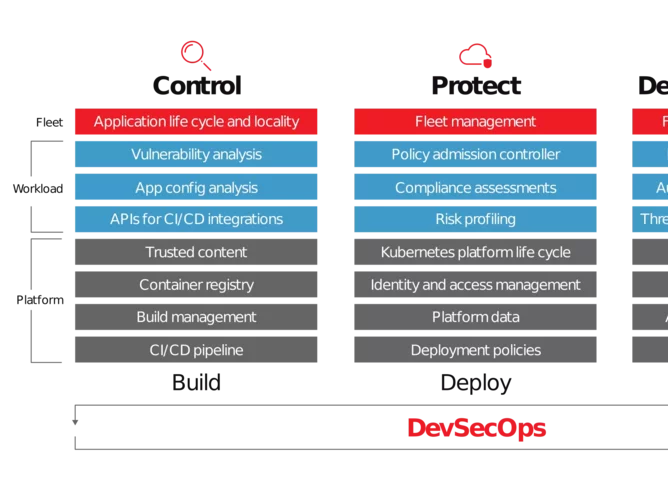
Ecosystem collaboration
The move to service-based, disaggregated architecture brings more complexity and more interfaces, which can potentially create a greater attack surface. There is less room for error as new technologies powered by 5G are deployed across a multitude of industries to support critical tasks in anything from emergency services to manufacturing.
To bring these applications to life and continuously adapt to meet the changing needs of customers and industries, service providers need to work closely with their suppliers to establish a secure supply chain. Governments and regulators are also stepping in here. The industry needs to embrace greater collaboration to circulate best practices, such as establishing appropriate levels of privilege for applications running on shared infrastructure rather than requiring privileges by default.
This means working in the open to agree on security processes and protocols across identity and access management, network controls, data controls, compliance and more. It also means becoming more adept at working with open source software, which provides the benefit of having many eyes reviewing the code, identifying risks and vulnerabilities and working on fixes to create robust solutions.
Once we have alignment on security best practices based on collaboration between 5G network functions providers and the suppliers of infrastructure, security automation can be used to enforce these practices and easily modify them over time using for example a GitOps approach and Kubernetes operators.
Securing the next generation
As 5G rolls out and becomes mission-critical for many industries via technologies like the Internet of Things, it is ever more important for service providers to take an agile approach in collaboration with those all along the supply chain. By working together to ensure consistent security best practice from core to edge, in every aspect of the network and the application, the ecosystem can deliver the most seamless and consistent experience for the end user.






